I’ve been writing posts keeping track of Bluesky development for you all. If you haven’t been following along, Bluesky is a social network, roughly in the style of Twitter. It was hip and new last year. Maybe it will be hip and new again now! Why? Because you can finally sign up without an invite. While it lacks some of the features that more mature services have, like video uploads, it is also not thoroughly saturated with nazis and crypto scam bots, and does not promote the posts by the biggest dumbasses in the world everywhere you go. I think that’s an acceptable trade-off.
I’ve been writing posts keeping track of Bluesky development for you all. If you haven’t been following along, Bluesky is a social network, roughly in the style of Twitter. It was hip and new last year. Maybe it will be hip and new again now! Why? Because you can finally sign up without an invite. While it lacks some of the features that more mature services have, like video uploads, it is also not thoroughly saturated with nazis and crypto scam bots, and does not promote the posts by the biggest dumbasses in the world everywhere you go. I think that’s an acceptable trade-off.
More importantly, it has what I think is a true killer feature–custom feeds. Anybody can make one, and you can subscribe to them and have them live natively in the app, and have their posts inserted into your chronological feed. At their most basic they’re just posts from a list of users, but more advanced ones surface content via hashtag or emoji, or an AI recognizing pictures of cats or flowers, etc. There are even several good algorithmic recommendation feeds to choose from, in addition to the default one run by Bluesky itself.
It’s also allegedly going to open to federation this month; click the link at the top of this post for details on how that will work.
There’s a lot more great stuff in the pipeline. Composability will be the name of the game–choose your algorithms, choose your moderation services, choose your host, choose whatever you want. Here’s what WaPo has to say:
That system is a work in progress. So far, Bluesky is the only social network using its protocol. But it already has some features that set it apart. […] For instance, users can subscribe to feeds where algorithms prioritize the most popular posts overall or the posts most popular among the people they follow. There are also options for feeds geared to their specific areas of interest, such as science or art. And users can toggle personal moderation settings that either “hide,” “warn” or “show” categories of content such as nudity, violence, spam and hate-group iconography.
Along with today’s public launch of Bluesky, the company said it will roll out in the coming weeks a step toward its broader vision, inviting some outside developers to host servers that plug in to the main Bluesky network. It also announced a new feature that will let users and organizations begin todevelop their own content moderation services, which other users can then subscribe to. For instance, a fact-checking organization could apply “false” or “misleading” labels to certain posts, which would then be seen by users who opt in to seeing them.
With that out of the way…
A guide to getting started at Bluesky
- Sign up at bsky.app!
- Give yourself a profile picture and bio. Anything will do, really; it helps set you apart from other users and makes you more approachable.
- Find some custom feeds. It’s in the left column on desktop, or the hashtag icon on the bottom on mobile. I recommend:
- For You, a third-party recommendation algorithm
- Discover, the official recommendation algorithm
- Popular with Friends, an official feed of… things that are popular with your friends.
- Gardening
- Food
- Science
- Cats and Cat Pics
- A few dozen folks are reading A Wizard of Earthsea for book club this month, you can see some posts about it here, and add your own thoughts by posting about Earthsea, #bskybc, or Gontishmen.
- And, of course, Newskies, where you can see the first post by every new user in real time.
- Under Moderation -> Content Filtering, you can set your preferences for showing/warning/hiding NSFW stuff, hate group iconography, gore, etc.
- Note that they’re still working out the, ah, kinks, and you might see some NSFW stuff slip through the filters.
- If you signed up on iOS, all mature content is removed from your feed by default; this cannot be changed from your iPhone. Log in at bsky.app and change your preferences there.
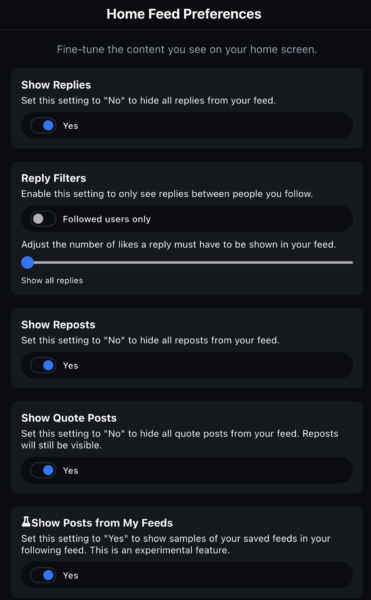
- Speaking of changing your preferences: I recommend this at Settings -> Basics -> Home Feed Preferences. It will show all posts by people you follow, including when they’re replying to somebody. The one at the bottom is important too–it inserts select posts from your feeds into your chronological following timeline. I also recommend Threaded Mode at Settings -> Basics -> Thread Preferences.
- Almost everything you do is public on Bluesky, but you can set it so that people have to be logged in to see your posts under Moderation (not in preferences) -> Logged-out visibility, which includes some important caveats in the description.
- I maintain a large moderation list of authoritarian communists, Russia simps, etc. I recommend subscribing to it, which will block or mute everybody on it.
- Post, post, post! And reply to people, politely of course. It’s the recommended way to get noticed.
You can find me at @thearchduke.bsky.social. Many other jackals are there, please share in the comments. Plus:
Happy posting!
Bluesky is now open! Sign up today! (A guide to getting started)Post + Comments (63)